Get ready for some statistics that will only confirm your worst fears. In Sophos’ The State of Ransomware 2022 report, 66 percent of the 5,600 IT pros in 31 countries surveyed said they had been hit by ransomware last year. Let that sink in. It gets worse: 65 percent of those attacks resulted in the organization’s data being encrypted. Of those, 46 percent paid the ransom. And only 4 percent of those that did pay got all their data back.
Cybercriminals are getting smarter, too, offering ransomware as a service (RaaS) to specialists whose skills in “virtual breaking-and-entering,” as Sophos puts it, differ from those of ransomware creators. An alert from the Cybersecurity and Infrastructure Security Agency (CISA), part of the National Security Agency (NSA), notes that for one RaaS called Conti, bad actors often try to gain initial access using spearphishing campaigns with tailored emails containing malicious attachments. But they’ve got plenty of other burglary tools up their sleeve. Among those listed by CISA:
- Stolen or weak Remote Desktop Protocol (RDP credentials)
- Phone calls—yes, some hackers will even cold-call a company to try to wring the information from employees they need to get onto your network
- Fake software promoted via search engine optimization (SEO)
- Malware distribution networks like ZLoader
But here’s the real kick in the teeth: the Sophos report says the average cost to remediate a ransomware attack was $1.4 million, and the average time it took to recover from an attack was one month. One final note on Conti ransomware, with the headline of a recent Threatpost article saying it all: “Conti Ransomware Expands Ability to Blow Up Backups.” Your backups aren’t safe from ransomware either.
Add it all up, and you can bet you’re only a click on a malicious link away from a potentially devasting ransomware attack on your organization.
IT Transformations Add Complications
You need to do everything you can to fight back against ransomware. But that isn’t easy with today’s increasingly complicated IT infrastructures. You may have a hybrid workforce using personal devices to connect to your network. And with IoT prevalent across many industries, you may be dealing with a massive increase in attack surfaces and vulnerabilities. Then there are your servers, endpoints, networks, network-attached storage, clouds, applications, and more that all need to be protected from ransomware.
With so many potential vulnerabilities and evolving attack vectors, IT pros need to change their approach. Beating ransomware requires a multi-faceted prevention strategy. No single silver bullet will keep ransomware at bay, especially given that there are so many other threats to your data, from malware to natural disasters.
The Three Pillars of a Complete Ransomware Prevention Strategy
We recommend a ransomware prevention strategy based on three pillars:
- Cybersecurity technologies
- Orchestrated recovery
- Security processes
1. Cybersecurity Technologies
Cybersecurity is a crucial aspect of your multi-faceted ransomware prevention strategy. It includes ensuring you have the latest protections for your endpoints, networks, servers, and other infrastructure elements.
At a minimum, it’s worth adding Identity Access Management (IAM) to keep unauthorized users out and Privileged Access Management (PAM) solutions to limit access to sensitive data based on roles. As we wrote in a recent post, you can take your defenses even further by employing a zero-trust model for data protection.
In the same post, we also make a case for putting advanced monitoring functionality in place so your backup admins can react quickly to any threats or other issues involving your primary or backup infrastructure and operations. That includes data loss prevention (DLP) software that detects potential data breaches and data exfiltration activities and then blocks them from accessing sensitive data—in use, in motion, and at rest.
Endpoint detection and response (EDR) is another cybersecurity tool that continuously monitors end-user devices to detect and respond to cyber threats. If your organization uses a remote or hybrid work model, EDR is invaluable.
Plenty of other cybersecurity tools and solutions are available. See this post for links to tools offered by the NSA and CISA to combat open-source cyberthreats. And check out this post in which we dive into how you can create a more resilient organization (starting with a cyber resilience review). We also offer a host of links to valuable—even essential—tools that will help you raise cybersecurity awareness and ensure business continuity.
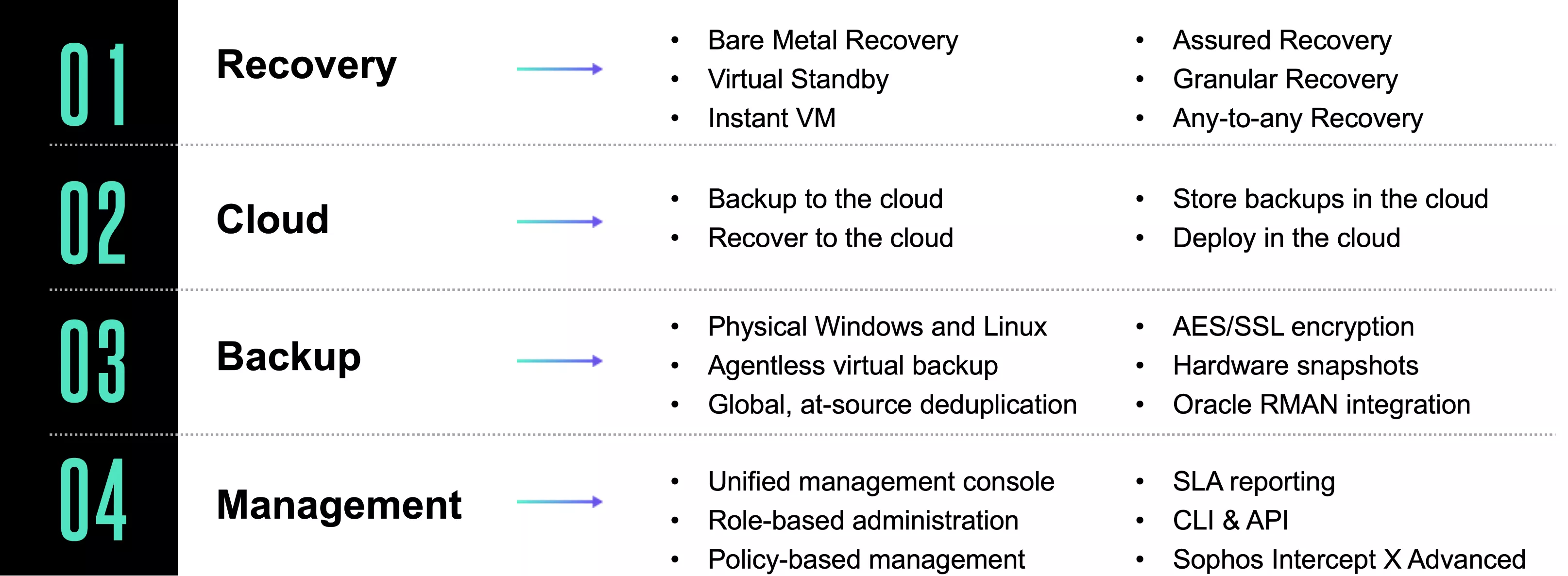
2. Data Protection and Orchestrated Recovery
The most important step you can take is to ensure your backups are protected from encryption and exfiltration. Arcserve strongly recommends that you follow the 3-2-1-1 backup strategy. (The 3-2-1 backup rule is out of date now that backups are being targeted more frequently by ransomware.) The rule is simple: keep three copies of your data; store two copies locally on two formats (tape, network-attached storage, or local drive); and keep one copy offsite, with the cloud offering the most flexibility. The extra one stands for immutability. Backups saved or replicated to an immutable object store are in a write-once read-many-times format. These immutable backups can’t be altered or deleted, so they are safe from ransomware no matter what.
If you are hit by a successful ransomware attack or other data loss event, orchestrated disaster recovery will help you recover as efficiently as possible. An effective orchestration solution also ensures that your critical systems—servers, applications, and sensitive data—are automatically brought back online in the proper order. That takes much of the complexity out of recovery. Given the multiple tasks that go into a manual failover, orchestration ensures fast disaster recovery, even as you scale your organization.
3. Security processes
The final pillar may be the most critical because the human element was involved in 85 percent of breaches in 2021. Tools and solutions aren’t enough. Cybersecurity training should be a core element of your disaster prevention and recovery plan. CISA offers an excellent cybersecurity awareness program that includes a toolkit and resources. Make sure your team understands how to spot phishing schemes and suspicious links. Help them know how vital their role is in preventing ransomware and breaches.
It's also essential to run disaster recovery exercises that test your disaster recovery plan’s effectiveness. And don’t forget to keep physical security in mind, including running background checks. Finally, we want to reiterate the value of IAM and PAM in keeping your data secure.
Arcserve UDP: Key Differentiators Make All the Difference
When it comes to ransomware, Arcserve UDP stands out because it offers all-in-one data and ransomware protection, data restoration, and effective disaster recovery (DR). Here’s what Eric Burgener, Research Director for IDC’s Storage Practice, says about UDP: “The concept of unified data protection brings significant value to enterprises that are struggling to meet increasingly stringent RPOs and RTOs across physical, virtual and cloud environments. Burgener continues, “Economics will drive data protection consolidation as administrators look to simplify how they handle backup, recovery, and business continuity requirements in today's heterogeneous world.”
Arcserve UDP is the only vendor that delivers on the economic promise of consolidation by preventing ransomware across your entire IT infrastructure with proven data protection and industry-leading cybersecurity across hardware, cloud services, and software.
Ransomware Prevention Plus Advanced Security
Arcserve UDP includes Sophos Intercept X Advanced for Server, providing you with a comprehensive solution that can block ransomware and malware—even zero-day attacks—and protect your critical backup infrastructure.
Intercept X Advanced includes anti-hacker and anti-exploit technologies that actively hunt down evasive threats using a deep learning neural network combined with signature-based protection from common threats. With Sophos’ endpoint detection and response (EDR), Arcserve UDP gives you unmatched visibility into your servers. And you can quickly create policies for threat protection, application, peripheral, and web control, then apply them with a few clicks across your infrastructure or to protect specific, individual servers. That includes changing multifactor authentication (MFA) and privileged access management (PAM) policies as roles change.
Backup Storage Flexibility
Arcserve offers seamless storage for your UDP backups, with Arcserve OneXafe appliances offering immutable backup storage to support your 3-2-1-1 backup strategy. With UDP, you can quickly scale hybrid business continuity topologies—locally or over long distances across multiple sites—including service and cloud providers.
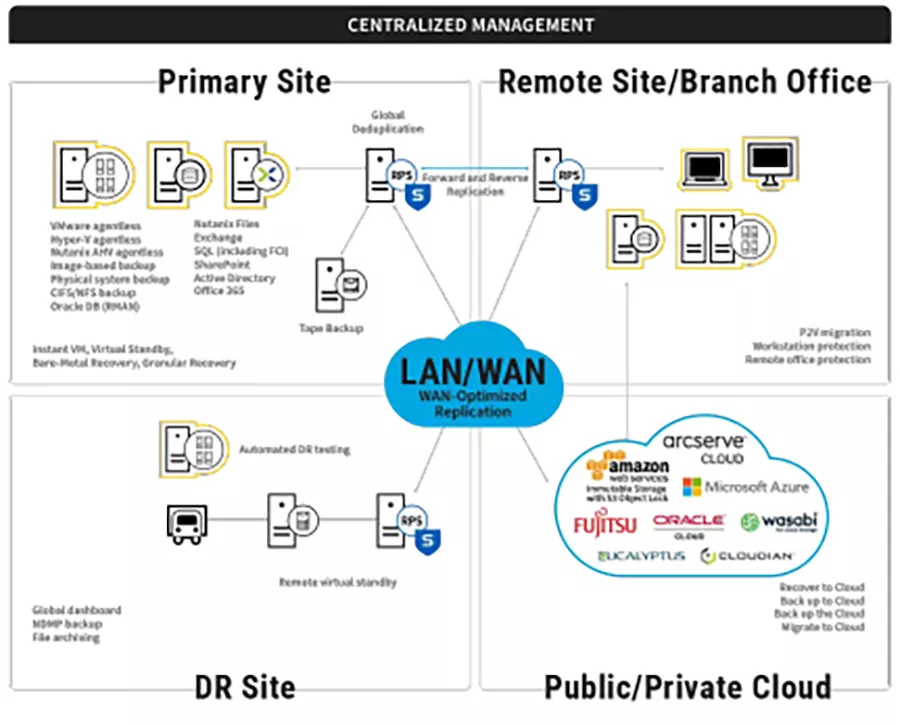
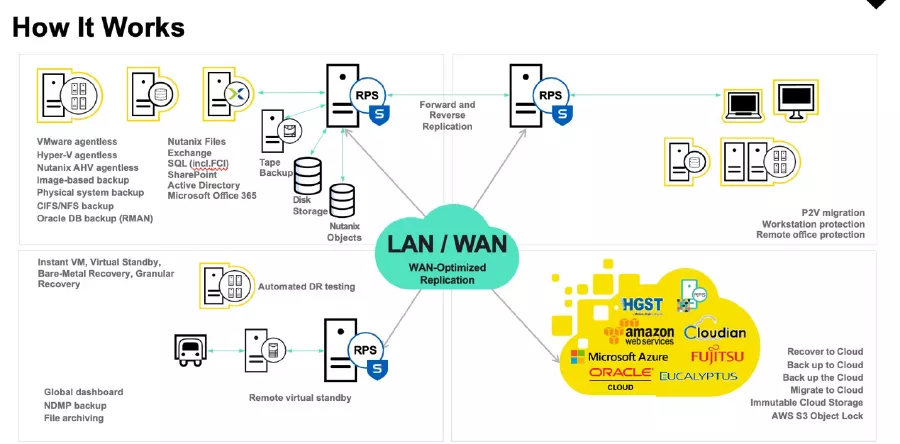
Installation is as simple as making a few clicks. And centralized management lets you create data stores on the recovery point server, add the nodes you want to protect, a storage destination, and a plan. UDP also makes it easy to perform backups, virtual standby, and replication, as well as a simple restore or bare metal recovery. You can back up to a local machine or a central recovery point server (RPS) with global, source-side deduplication. A destination can be an RPS, local folder, or remote shared folder. And its easy to add network CIFS/NFS shares, Office 365 Exchange, or SharePoint online nodes.
Arcserve OneXafe Immutable Storage
With Arcserve OneXafe, you get native immutable network-attached storage (NAS) to protect your backups. Every object is written once and never modified, with any changes you make to your file system always resulting in the creation of new objects. OneXafe continuous data protection (CDP) takes low-overhead snapshots every 90 seconds, enabling you to go back to specific points in time and recover entire file systems in minutes. As a scale-out NAS solution, OneXafe makes it easy to add capacity seamlessly, one drive at a time or multiple nodes in a cluster. And OneXafe’s unified architecture makes management easy, and it includes enterprise features like inline deduplication, compression, and encryption at rest.
Immutable Cloud Storage
Arcserve UDP delivers immutable cloud storage powered by Amazon AWS S3 Object Lock and S3-compatible storage systems like Nutanix Object Lock and Wasabi Object Lock. With immutable cloud storage, your backups are safe from being altered or deleted by ransomware, malware, or hackers.
Benefits Beyond Backups
Arcserve UDP stands out because it protects your entire IT infrastructure and secures your data backups. But the benefits go far beyond those crucial basics. UDP delivers orchestrated recovery, giving you automated, orderly recovery of your server environment following an outage and prioritizing your critical servers, applications, and data for recovery first. Orchestrated recovery can enable you to reduce your recovery time actual (RTA) and recover point actual (RPA) to minutes.
UDP features Assured Recovery, which detects physical and logical corruption of Oracle source data, ensuring the recoverability of critical database backups so that you can validate SLAs with confidence. Add it all up, and Arcserve UDP reduces complexity, reduces your costs, and ensures you can recover from just about any disaster.
Under the Hood of Arcserve UDP: How Unified Data Protection Works
We built UDP so you get fast, simple, efficient data protection and orchestrated recovery from ransomware. But UDP has a long list of other features and benefits that further deliver on that promise.
Unified Management Console
Using a simple, single, web-services-based console, manage your entire Arcserve UDP environment—including node, group, and backup and disaster recovery plan management. Deployment, day-to-day management, and reporting are all made easier with wizards that get you started for each setup process.
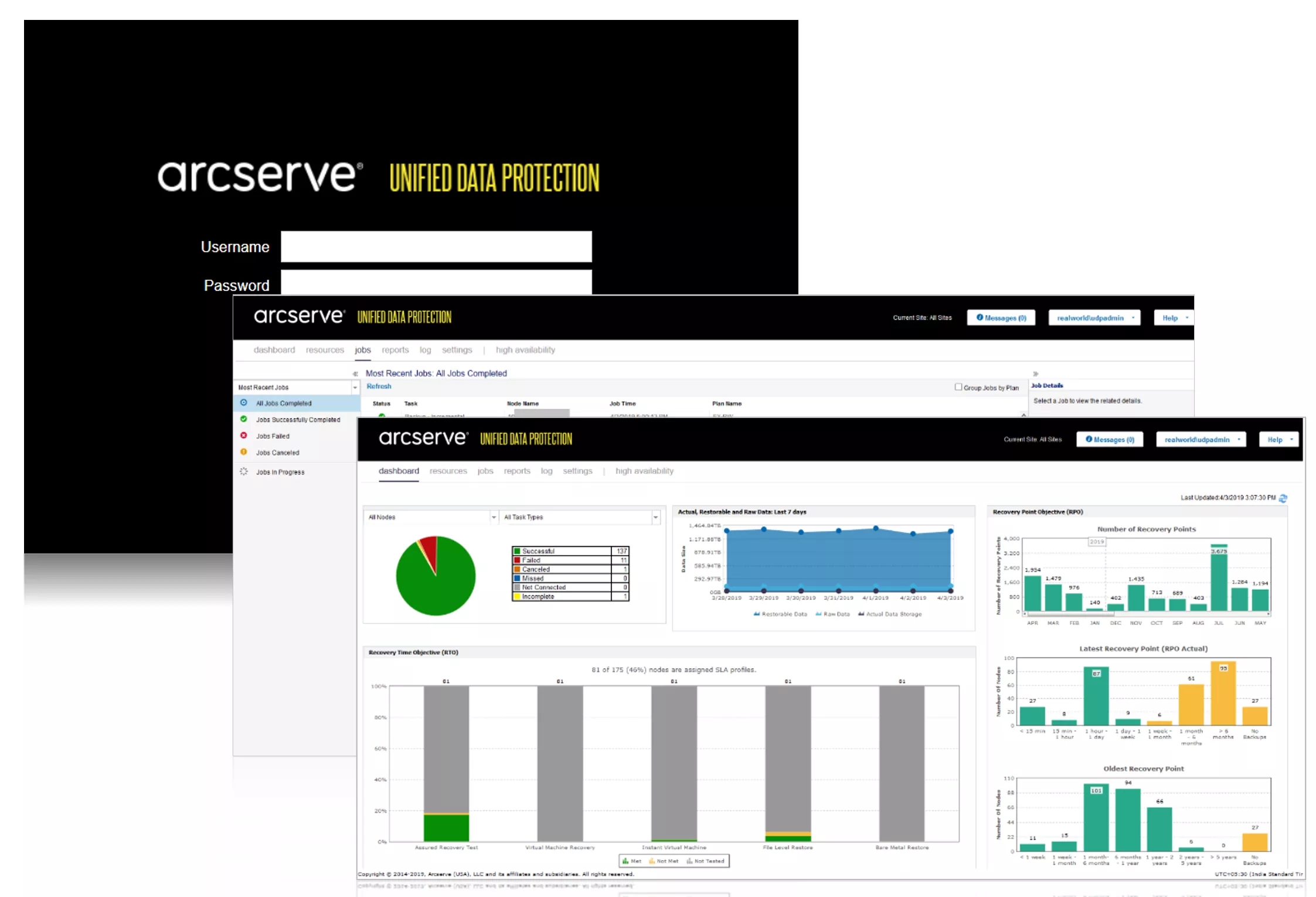
Plan-Based Data Protection Policies
UDP’s unified management console manages the entire data protection lifecycle. And it uniquely gives you the capability to create intuitive, workflow-based data protection and availability strategies that form the basis for your organization’s protection and availability plans. Compare that efficiency level to traditional data protection solutions in which admins are forced to protect highly complex environments using disjointed and ever-growing lists of backup, replication, and failover policies—often across multiple products or systems.
Armed with your data protection and availability plans, the UDP unified management console makes it easy to put robust, plan-based data protection policies in place. The UDP management console also gives you detailed reporting and logs and is designed to extend your capabilities with third-party integrations.
Multi-Factor Authentication (MFA)
Arcserve UDP requires users to input multiple factors to be successfully authenticated. Microsoft and Google say that using MFA can potentially block up to 99.9 percent of automated account-hacking attacks.
Physical and Agentless Backup
Arcserve UDP makes it easy to quickly back up multiple legacy and modern workloads, including integrating agentless host-based backup for Nutanix AHV, vSphere, and Hyper-V host environments. UDP also:
- Enables single-pass backup of all VMs, without the need to install software agents
- Only backs up changed blocks, reducing traffic and storage requirements
- Ensures application-consistent backups for Exchange, SQL, Active Directory (AD), and other platforms
- Automates protection of newly added VMware and Nutanix VMs
- Makes it easy to recover individual files and folders from within each VM
Deduplication, Encryption, Compression, and Replication
UDP reduces storage consumption and network bottlenecks with source-side global deduplication, encryption, compression, and wide-area network (WAN) optimized replication. Global deduplication gives you recovery point server (RPS) capacity-optimized backups and:
- Eliminates the need for a second full backup
- Uses less disk space and network bandwidth, with a recent IT Pro review finding UDP’s global deduplication and compression to be highly efficient, taking a total of 1.9TB of data from all nodes and compressing it down to just 304GB, calling it “an impressive 84% data reduction”
- Offers enhanced cloud integration and cloud recovery in Amazon environments
- Works with software, appliance, and cloud solutions
Faster Data Restoration Options
UDP’s instant virtual machine and bare metal recovery (BMR) capabilities can restore your data faster. You also get automated local and remote virtual standby to meet your RPOs and RTOs locally or over a distance. Virtual standby converts your recovery points to virtual machine formats and prepares a snapshot that lets you easily recover your data when needed. This feature delivers high availability and ensures that the virtual machine can take over immediately when the source machine fails. Virtual standby:
- Provides application and data protection for physical servers and VMs using a periodic, image-based system
- Replicates to remotes locations such as remote offices, disaster recovery (DR) sites, managed services providers (MSPs), and the cloud
- Runs recovery point conversion into a virtual server at the remote site—in virtual hard disk (VHD), virtual machine disk file (VMDK), Nutanix AHV, or AWS EC2 formats.
- Registers with the hypervisor
- Includes server heartbeat monitoring
- Enables automated or manual failover to remote resources
The same IT Pro review cited above tested Arcserve UDP’s file and folder recovery capabilities and found that restoring the files to the host or with Exchange Online recovery was a smooth, easy process. The reviewers also say that UDP’s Instant VM feature is excellent for fast system restores through creating on-demand VMs from node recovery points. It only took the reviewers 210 seconds to use the appliance’s Hyper-V services to get a new VM up and running.
Hardware Snapshots and Backup Options
With Arcserve UDP, you can integrate hardware snapshots into your existing storage infrastructure. Switching to this backup strategy:
- Enables frequent, high-performance, low-impact, and compact snapshots of physical and virtual environments
- Stores hardware snapshot-based backups on your RPS to take advantage of global deduplication
- Tightly integrates with your host environment to ensure application-consistent backups and reliable granular restores
- Delivers a simple, fully automated snapshot orchestration process (creating, mounting, deleting, etc.)
- Supports NetApp, HPE 3PAR, and Nimble for agent-based backup in Windows physical machines and agentless backup in Hyper-V environments
- Supports Dell EM Unity for agentless backup in Hyper-V environments
- Performs fast, image-based backups to local disks and scheduled backup of recovery points to tape at local or remote sites—and even supports granular restores directly from tape
Broad Platform Support
Arcserve UDP protects your data across a long list of platforms:
- Windows
- Linux / Red Hat Enterprise Linux / CentOS /Oracle Linux Server
- File servers
- Amazon EC2
- Microsoft Azure
- Office 365 (Exchange Online, Teams, SharePoint Online, and OneDrive for Business)
- Microsoft Exchange
- MS SQL
- Microsoft IIS
- Microsoft Active Directory
- Native Oracle Database integration with RMAN
- Oracle 19c
- VMware vSphere (agentless)
- Microsoft Hyper-V (agentless)
- Debian
- Nutanix AHV
- Nutanix Files
Click here to view Arcserve UDP 8 complete software compatibility matrix.
It All Adds Up to Better Data Protection
Arcserve UDP has been recognized as a leading data protection solution because it gives you the options you need in a single, simple solution.
You don’t have to wait to see how Arcserve UDP can make a difference for your organization. Check out our no-obligation 30-day free trial or choose an expert Arcserve technology partner to help get started with unified data protection today.
You May Also Like
- Backup and Disaster Recovery Business Continuity Cloud Compliance Cybersecurity Data Protection Data Resilience Data Storage Ransomware
The Importance of Versatile Cloud Data Protection Support in a Multicloud World
December 3rd, 2024 - Backup and Disaster Recovery Business Continuity Cloud Compliance Cybersecurity Data Protection Data Resilience Ransomware
The Vital Role of Replication in Ensuring Data Resilience
November 20th, 2024 - Backup and Disaster Recovery Business Continuity Cloud Cybersecurity Data Protection Data Resilience Ransomware
Why Flexible Disaster Recovery Matters In a Hybrid World
November 12th, 2024